Using google DORK try to find the vulnerable website.
inurl:"/portals/0"
You can also modify this google dork according to your need & requirement
I have found these 2 website vulnerable to this attack:http://www.wittur.se/
http://www.b
n00bs can also try both of these websites for testing purpose.
Open the home page and check any image which is located in /portals/0/
Check the location of the image. It should be located in /portals/0/
For e.g. in case of http://www.wittur.se ..the image is located at location- http*://www.wittur.se/Portals/0/SHM.jpg*
Rename the new image as SHM.jpg which you want to upload as a proof of you owned the system.
Now here is the exploitProviders/HtmlEditorProviders/Fck
Simply copy paste it as shown below:www.site.com/Providers/HtmlEditorP
You will see the portal where it will ask you to upload. Select the third option File ( A File On Your Site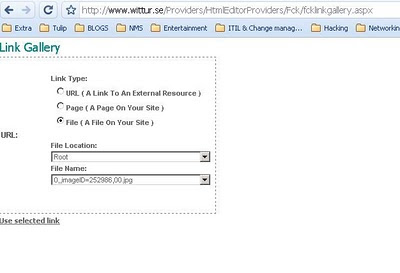
After selecting the third option, replace the URL bar with below script
For script click here http://tinypaste.com/af8b9
After running this JAVA script, you will see the option for Upload Selected File Now select you image file which you have renamed as SHM.jpg & upload here. Go to main page and refresh...BINGGOOOOOOOOOOOO you have hacked the website.

inurl:"/portals/0"
You can also modify this google dork according to your need & requirement
I have found these 2 website vulnerable to this attack:http://www.wittur.se/
http://www.b
n00bs can also try both of these websites for testing purpose.
Open the home page and check any image which is located in /portals/0/
Check the location of the image. It should be located in /portals/0/
For e.g. in case of http://www.wittur.se ..the image is located at location- http*://www.wittur.se/Portals/0/SHM.jpg*
Rename the new image as SHM.jpg which you want to upload as a proof of you owned the system.
Now here is the exploitProviders/HtmlEditorProviders/Fck
Simply copy paste it as shown below:www.site.com/Providers/HtmlEditorP
You will see the portal where it will ask you to upload. Select the third option File ( A File On Your Site
After selecting the third option, replace the URL bar with below script
For script click here http://tinypaste.com/af8b9
After running this JAVA script, you will see the option for Upload Selected File Now select you image file which you have renamed as SHM.jpg & upload here. Go to main page and refresh...BINGGOOOOOOOOOOOO you have hacked the website.







![[Image: 2viffd5.jpg]](http://i47.tinypic.com/2viffd5.jpg)
![[Image: 59925653.jpg]](http://img8.imageshack.us/img8/1192/59925653.jpg)
![[Image: 2iql3ex.jpg]](http://i46.tinypic.com/2iql3ex.jpg)
![[Image: 2yuk7cg.jpg]](http://i48.tinypic.com/2yuk7cg.jpg)
![[Image: vwu8ud.jpg]](http://i47.tinypic.com/vwu8ud.jpg)
![[Image: 317a8tf.jpg]](http://i46.tinypic.com/317a8tf.jpg)
![[Image: x3vfuw.jpg]](http://i48.tinypic.com/x3vfuw.jpg)
![[Image: 2d1x0uh.jpg]](http://i45.tinypic.com/2d1x0uh.jpg)
![[Image: rlgoqo.jpg]](http://i47.tinypic.com/rlgoqo.jpg)
![[Image: 6s6us6.jpg]](http://i50.tinypic.com/6s6us6.jpg)
![[Image: 214wq3m.jpg]](http://i46.tinypic.com/214wq3m.jpg)
![[Image: 2qvyx4n.jpg]](http://i47.tinypic.com/2qvyx4n.jpg)
![[Image: 15x8g1j.jpg]](http://i47.tinypic.com/15x8g1j.jpg)
![[Image: 9i9xdk.jpg]](http://i47.tinypic.com/9i9xdk.jpg)
![[Image: ibayw9.jpg]](http://i50.tinypic.com/ibayw9.jpg)
![[Image: 142hv09.jpg]](http://i46.tinypic.com/142hv09.jpg)
![[Image: 17detv.jpg]](http://i49.tinypic.com/17detv.jpg)
![[Image: 29wv9yb.jpg]](http://i50.tinypic.com/29wv9yb.jpg)